The modern method of carrying out banking transactions from a PC or mobile device is ever more popular. Around half of all Internet users in the EU (48%) use online banking services. Financial transactions are among the most sensitive online procedures and, naturally, security is of the utmost priority here. To users, Security (96%) and data protection (94%) are the most important factors when it comes to online banking.*
In times of ceaseless reports about security issues such as “Heartbleed”, “Panama Papers” and similar issues, financial service providers, hosts, administrators and users etc. are vital links in the chain of making a process smooth and secure. G DATA experts have put together the following tips and recommendations to ensure that digital bank transactions run smoothly. Security and convenience are not mutually exclusive in this case.
What you need to look out for, especially with transfers etc.
87% consider the use of a publicly accessible PC to be a risk.*
Only use online banking services on devices you know and trust. Perform transactions in secure environments only.
Computers in an internet café do not fall into the category of “secure devices”. Doing online banking over a public Wifi network is akin to moving across a digital minefield. Users have no control over the security of third-party and (especially) public computers. Hence it must be assumed that, at worst, they are infected with malware that can steal input access data, for example, or specifically target online banking customers.
Open WLANs are not secure because the data traffic can be very easily intercepted and read. This means that the input data is not safe from attackers. The use of password-secured networks and encrypted transfer protocols (e.g. universal HTTPS) is a first step in the right direction towards better security. Using a VPN tunnel is the only way to isolate all data traffic from being snooped on by attackers without interrupting it (thus giving the attacker away).
For 59% of participants in our survey, the use of personal devices is an important step in increasing security when using online banking services.*
Enter the service provider’s web address manually, or use a bookmark
Attackers exploit the inattentiveness of potential victims and coax them into visiting websites that look and feel similar to the original website so they can carry out phishing or malware attacks.
Assume there is a bank with the domain name “MyPersonalBank.com”: Attackers would for example register a domain called “MyPersonaIBank.com”. It is not at all visually apparent that the lower case “l” in “Personal” has been replaced with a capital “i”. Inattentive users can be lured into this trap when such a trick is used in spam emails or on websites. The use of HTTPS instead of HTTP is also important.
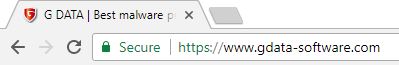
Keep an eye on the security features in your browser
Modern browsers use colours and icons to indicate whether a connection between the browser and the web server is secure and whether the certificate provided is valid.
Use a sufficiently secure process to authorise payments
On this point, choosing an appropriate payment authorisation process such as a transaction number (TAN) is generally important. The HBCI/FinTS process is also an option. There are several processes that each have advantages and disadvantages – various banks have their own favourites and advise their customers on the options appropriate to them in the branch.
As a rule of thumb, conventional TAN lists and iTANs should no longer be used for security reasons. The SMS-TAN and mTAN processes are OK, but not suitable if the TAN is received on the same device as the one where the banking transaction is being carried out. The use of TAN generators with their manifold possibilities has now been implemented in many banks for their private customers. This approach currently represents the most viable solution in terms of user-friendliness, security and cost.
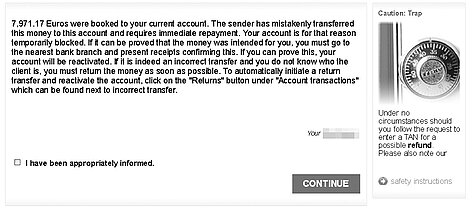
Do not trust sudden pop-ups on the service provider’s website
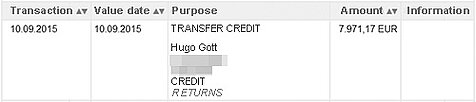
Some banking Trojans specialise in carrying out attacks using technological and social engineering techniques. They use so-called web injects to display additional content on a website to the victim, such as a test transaction or an allegedly failed credit to your account.
The attackers claim that the victim must carry out a “return transfer” as the money does not belong to him/her. However, in reality there never was a credit – it is just a technical trick. The “return transfer”, however, is a perfectly normal transaction from the bank’s point of view and results in a deduction from the account.
After the online banking process, log out of the service
Many banking portals have now implemented an automated logout function which logs the user off after several minutes of inactivity. Logging out of the service is important as the current session is terminated and nobody can use technological means to take it over.
Check your account statements regularly and frequently
Irregular transactions should be apparent as soon as you look at an account overview. The first point of contact for clearing up the matter is your local bank. The terms and conditions of the financial provider will tell you what steps must be taken in what period to make a valid claim. Specific periods apply here in terms of the closing of accounts, which differ from account statements under law and must be carried out at least once a year.
34% of respondents say that they use a daily limit for online transfers for the security of their online banking.*
Set a maximum possible transaction amount for your online banking
Banks generally offer a function that can be used to set a limit for all transactions carried out offline and online. This allows you to determine what amount or sum can be transferred within a specified period as a maximum. Even though this might entail a loss of convenience, setting up a limit can reduce damages, should the worst happen.
Read your bank’s terms and conditions carefully
Even if reading such contracts is not your favourite pastime, studying the terms and conditions makes a lot of sense. Banks specify different requirements of their customers in respect of security precautions. Using an up-to-date security solution is either recommended or even mandatory by most banks. Furthermore, many financial institutes stipulate a legally permissible personal excess of €150 for customers in the event of a claim for damages. If gross negligence or fraudulent intent on the part of a user is proven, he might (certain cases excepted) be required to pay for all damages in full (Art. 675v of the German Civil Code).
General tips for security on the Internet
75% see the use of security software as a personal measure for increasing security when using online banking services.*
Equip your computer/smart devices with a comprehensive security solution
Antivirus software fends off malware before it gets onto a device. Innovative products with proactive technologies, Cloud connections and spam protection etc. offer optimum protection. All G DATA PC security solutions also include G DATA BankGuard for specific protection against banking Trojans.
Keep your devices and the software on them fully up to date
Security holes must be closed as quickly as possible so cyber criminals cannot exploit them for their attacks. G DATA security solutions with innovative Exploit Protection prevent the exploitation of security holes.
More than half of the users (54%) state that installing updates is a way of staying secure when using online banking services.*
Use strong, unique passwords
The access data for an account is of value in all respects and should be regarded as such. Every account requires a separate, strong password. A common mistake is for users to use their birthday as their PIN because it is easy to remember. It is easier if you use a secure password manager to remember the password for you.
Use multi-factor authentication as often as possible
A login name in combination with a password is the minimum requirement for secure access. It is better if additional login factors are used such as a biometric factor.
Only download your apps from trustworthy sources
User reviews, required permissions and the reputation of the app provider and the shop are all elements that should be checked before any download. G DATA Mobile Internet Security for Android checks the permissions of installed apps.
The number of users who also use mobile devices for online banking is increasing. 21% of respondents use a smartphone and 13% stated that they also carry out banking transactions via a tablet.*
Have a healthy mistrust of emails
Many attackers try to trap potential victims via email. To do so, they send mass emails that are frequently visual copies of original emails. The look is supposed to increase confidence that the links included are not dangerous (but are frequently used for phishing), and that attached documents have to be read urgently (in almost all cases those documents contain malware). Unfortunately, such social engineering attacks work all too often. Therefore, users need to be on their guard to be prepared for non-technical attacks as well. Financial services providers do not send important, personal messages via email.
* All statistics: Online Banking 2014 – Security counts! Preferences and requirements of banking transactions on the Internet – a D21 Initiative survey conducted by TNS Infratest (2014)
More information and sources
- Dridex – the comback king
- mTAN fraud relies on conventional Trojans